While writing scripts it can be needed to access resources we don't have privileges to reach with our ids and for which we need to use others.
Thanks to PowerShell it is possible to automate a script without having to write each time or to insert a clear password of a user in the script. In addition Power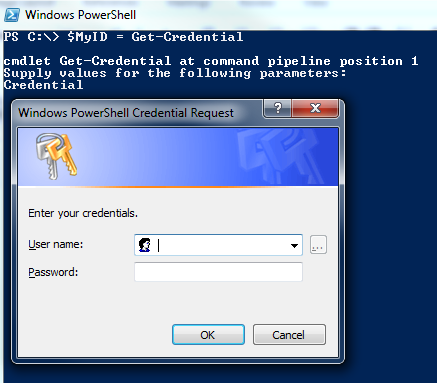 Shell is offering us the abality to secure the password.
Shell is offering us the abality to secure the password.
Here is an example on how to do get this working.
First we declare a variable in which I insert the ids to use.
PS C:\> $MyID = Get-Credential

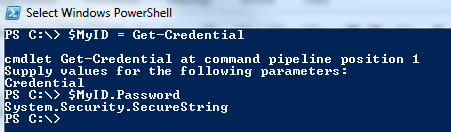
Then if we call our variable with the ‘Password’ object we see this is a ‘SecureString’.
PS C:\> $MyID.Password
In order to export the password in an encrypted file that we will use later we use the ‘ConvertFrom-SecureString’ function.
PS C:\> $MyID.Password | ConvertFrom-SecureString | Out-File D:\temp\ArnaudScriptTest\EncryptedPWD.txt
And here is the content of the file that we will use in order to create a PSCredential object which will have the username and the password encrypted in the file as arguments.

PS C:\> $User = “MyUserName”
PS C:\> $File = "D:\temp\ArnaudScriptTest\EncryptedPWD.txt"
PS C:\> $MyCredential = New-Object -TypeName System.Management.Automation.PSCredential -ArgumentList $User, (Get-Content $File | ConvertTo-SecureString)
Once you reach this point you can use the $MyCredential variable which contains the PSCredential object giving access to the ressources with don't have access with our ids.
PS C:\> New-PSDrive -Name X -PSProvider FileSystem -Root \\nc0fsr02\NASTEST -Credential $MyCredential
This way we don't have to insert a clear password in the script but instead I use a file in which the password is encrypted. However with the method the script will only work with our own user ids because I didn't mention any encryption key during the encryption of the password. PowerShell will encrypt and decrypt the password by using the Windows Data Protection API. So the encrypted password that we will use in our script will only work with our user and on this specific server where the operation has been done. If we want the use those credentials on several servers and / or with several people then we need to specify a encryption key.
When we specify a key the AES encryption algorithm will be used and we will be able to user those credentials from any server with any user as long as we know which AES key to use.
Going back to the instanciation step with our credentials to be used.
PS C:\> $MyID = Get-Credential

Then we create a file in which we create a random encryption key.
PS C:\> $KeyFile = "D:\temp\ArnaudScriptTest\myAES.key"
PS C:\> $Key = New-Object Byte[] 32
PS C:\> [Security.Cryptography.RNGCryptoServiceProvider]::Create().GetBytes($Key)
PS C:\> $Key | out-file $KeyFile

Now we export the password that we well encrypt with the key.
PS C:\> $PwdFile = "D:\temp\ArnaudScriptTest\EncryptedPasswordWithKey.txt"
PS C:\> $MyID.Password | ConvertFrom-SecureString -Key $Key | Out-File $PwdFile
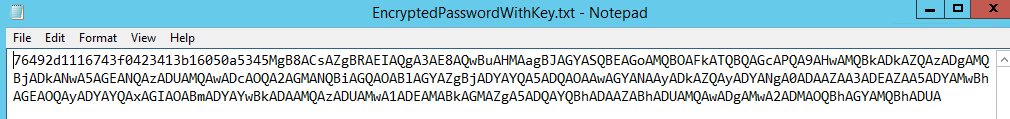
Here is what our password looks like once he is encrypted with a key.
Finally we create our PSCredential object which will contain the credential of the user that has access to the ressources we can't access with our personal ids.
PS C:\> $User = $MyID.UserName
PS C:\> $PwdFile = "D:\temp\ArnaudScriptTest\EncryptedPasswordWithKey.txt"
PS C:\> $KeyFile = "D:\temp\ArnaudScriptTest\myAES.key"
PS C:\> $key = Get-Content $KeyFile
PS C:\> $MyCredential = New-Object -TypeName System.Management.Automation.PSCredential -ArgumentList $User, (Get-Content $PwdFile | ConvertTo-SecureString -Key $key)
And now we can use the $MyCredential variable which contains the PSCredential object allowing the access to those ressources.
PS C:\> New-PSDrive -Name X -PSProvider FileSystem -Root \\nc0fsr02\NASTEST -Credential $MyCredential
We will now be able to use this key file to decrypt the password which is in a text file from any server with any user. We just need to take care of protecting tje key file because people that can read it can decrypt the key.
